Multiply your team’s effectiveness
40x faster overall response using dynamic playbooks that orchestrate your people, process and technology
IBM SOAR Platform integrates with all existing security systems to create a single hub for Incident Response, allowing easy workflow configuration and process automation to transform an organisation’s security posture. It empowers security teams to analyse, respond, resolve and mitigate incidents faster using consistent, intelligent processes.
One customer went from 20 days (on average) to close a security incident to less than 5 days – this was IBM.
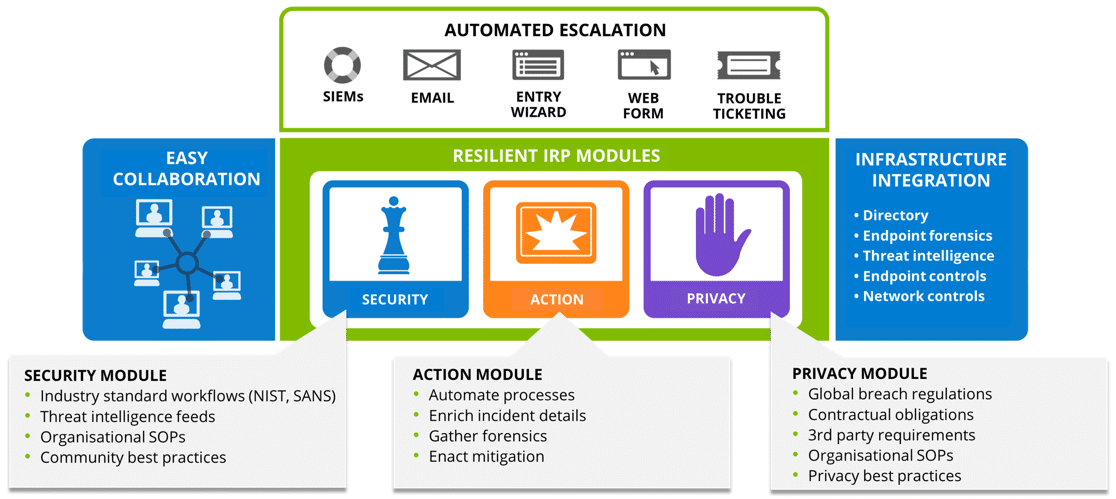
The life of a security incident
Although there is strong integration between QRadar and SOAR Platform, the infographic below on the life of a security incident is applicable to any SIEM.
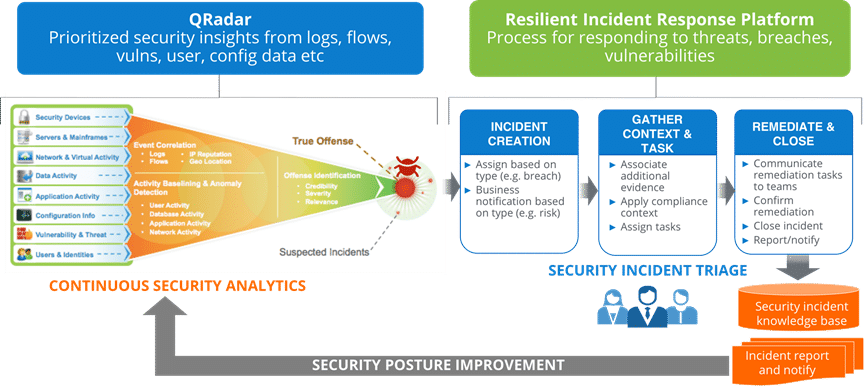
For a suspected malware outbreak and based on QRadar rules, an incident is automatically created inside IBM SOAR Platform, importing relevant information about the attack and any indicators of compromise (IoCs). SOAR will then generate a detailed response plan specific to the incident type and attaches any associated IOCs like the malware hash.
Leveraging automatic enrichment capabilities, the suspected malware is compared against threat intelligence feeds like IBM X-Force Exchange which confirms it is known bad malware and other characteristics such as linked phishing attacks and associated source IP addresses. These details can then be used to orchestrate remediation, like blocking the attack source through FW changes, helping to tune the SIEM tool to be more effective.
